Enterprise IT Security – Intelligent Managed Security Service To Solve Your Security Challenges

Bulletproof 365 Enterprise IT Solutions: 365° of Protection. Security that goes further.
There are gaps in your organization’s IT security right now. Mobile workforces, rogue mobile devices, shadow IT, hybrid cloud and on-premise infrastructure combined with a stack of tools that don’t communicate with each other are placing more demands than ever on IT teams.
Bulletproof 365 Enterprise is end-to-end Managed Extended Detection and Response (MXDR) security for Microsoft-powered organizations.
Our 24/7 IT managed security service comes in one cost-effective package—with no long-term commitments—to provide turn-key peace of mind for midsize businesses.
Enterprise-Grade Security to Maximize Your IT Power
If your IT department can’t keep up with the number of security events you’re alerted to each day, you’re not alone. Over 80% of companies with a high incidence of security alerts only have the resources to investigate 5% of these threats—or fewer.
Bulletproof 365E integrates robust protection with the world’s leading security software, Microsoft 365 and Microsoft Sentinel. Building on this strong security foundation, our team of Bulletproof IT experts offers continuous monitoring from an assumed-breach perspective. They analyze and correlate network events to pinpoint suspicious activity, investigate alerts, and effectively mitigate and contain potential threats.
With Bulletproof 365 Enterprise protecting your corporate network, your IT department will finally be free to focus on activities that drive greater value for your business.


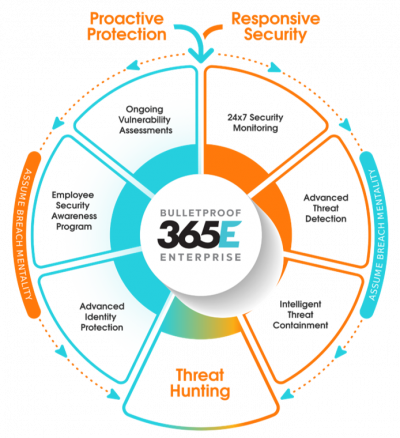
Up Your Cybersecurity with Bulletproof 365E
Why partner with Bulletproof for 365E security? Our service includes:
- Microsoft 365 Defender
- Advanced identity protection
- Automatic threat containment
- Proactive threat protection
- 24/7 responsive alerts & monitoring
- Employee security awareness training and enablement
Not only that, your data stays under your control and our cybersecurity experts free up your IT team. Discover how Bulletproof 365E can work for you.


“After we understood that we were indeed attacked we had Bulletproof on site and ready to support us in containment. When Bulletproof came on site, it was like they were part of the team; instant connection, working with them side by side.”
Stephaine Rackley-Roach, Chief Information Officer, City of Saint John




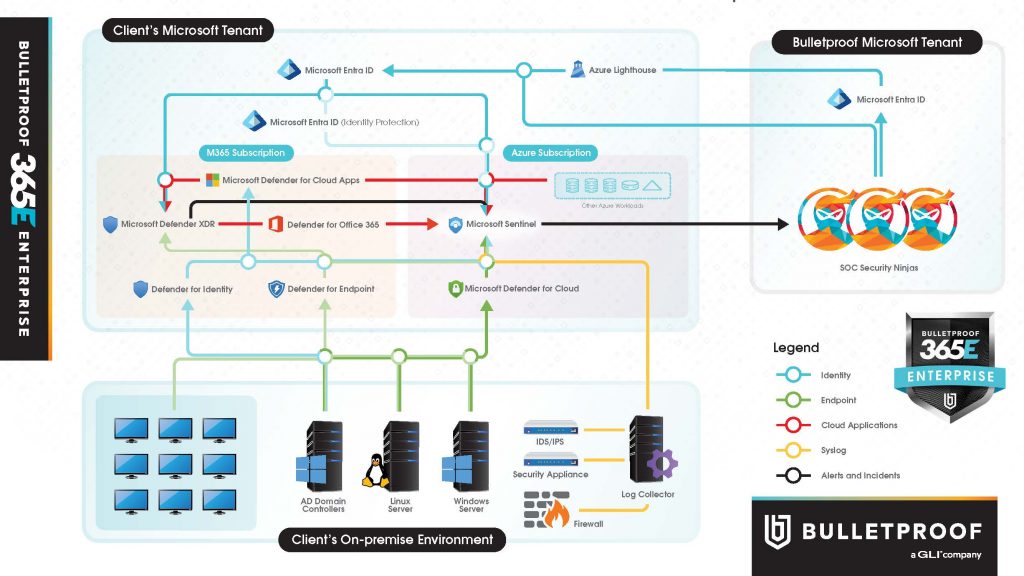
Reduce Risk with Best-of-Platform and Bulletproof 365 Enterprise
We designed Bulletproof 365 Enterprise to provide the most complete security visibility and incident response capabilities possible so that you can meet the requirements of the ever-changing digital security landscape.
The architecture diagram below illustrates just how integrated this solution is between Microsoft, Bulletproof, and your environment. This integration is the value of our solution; without any one of the components shown below, the integration, and therefore our security monitoring and incident response, suffers, leaving gaps in visibility and control.
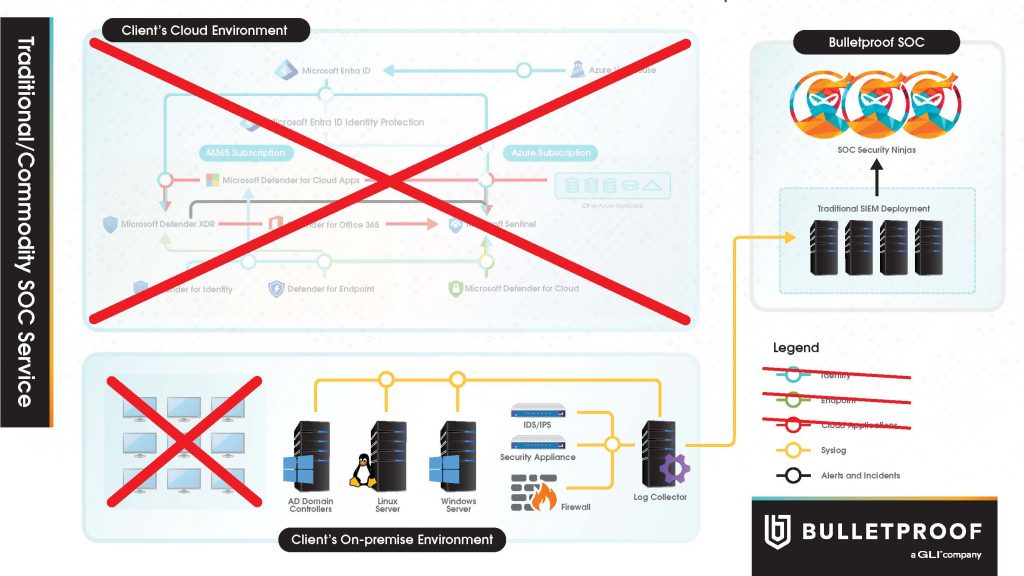
Traditional Security Information and Event Management (SIEM) Solutions
Traditional solutions lack integration and deployment of the complete Microsoft E5 Security stack, do not allow the same level of security monitoring and incident response; leaving room for blind spots and security gaps.
Legacy SIEM solutions can be appropriate for legacy environments but are not suitable for modern workplaces with modern productivity applications and services. Learn more about why Best-of-Platform is the better solution.

Bulletproof 365E: Seamless Integration with Your Existing Resources
Combine the power of your Microsoft 365 with Bulletproofs leading-edge data protection controls—including access management and advanced threat and breach detection. Our integrated solutions are designed to strengthen your organization against a spectrum of cyber threats, including malware, phishing attacks, and unsafe attachments that can lead to data breaches.
Our proprietary Security Aware training helps fortify what is traditionally the easiest target for advanced cybercriminals: your people.
We educate employees on cybersecurity and transform them into active defenders of your data. Our tool lets you customize, monitor, and update learning programs as you go. It also includes Microsoft 365 training resources to help increase user adoption.
Read the Bulletproof 365 Enterprise Solution overview to learn more.

How exactly do you weather a perfect cybercrime storm?
As the way we work has evolved, cybercrime tactics have evolved as well. How can you protect your business in an increasingly volatile cybercrime landscape? Take action with this eBook designed to help CEOs, executives, and decision-makers understand today’s cyberthreat and what they can do to tackle today’s challenges and strengthen their security posture.


We Help Our Clients Grow Their Business
The firm was losing revenue opportunities from high-profile clients who had specific security requirements. This, combined with staffing risks and a small internal IT team, meant they were looking for a Microsoft Partner that could provide an integrated security solution that would layer seamlessly with their technology and operations. Find out how Bulletproof’s managed security solution helped them win back the business of a top banking client.


If You Were Hit by a Ransomware Attack, Would You Know What to Do?
On Friday the 13th, in the middle of a pandemic, a cyberattack threatened to bring a city’s entire network—and crucial services—to a halt. Meet the city that refused to pay hackers and learn how quick action, teamwork, and the comprehensive visibility and security of our B365E solution saved the day.

Latest Resources

FIDO2, Passkeys, Passwordless and How to C…
ArticleDive deep into the world of modern authentication methods in this comprehensive piece where Anton guides you through configuring FIDO2 and implementing it effectively with Conditional Access Policies.


FIDO2, Passkeys, Passwordless and How to C…
ArticleLearn about passwordless authentication, FIDO2, Passkeys and discover how to configure and enforce strong authentication methods with Microsoft and Bulletproof.


7 Ways Microsoft Copilot for Security Will…
ArticleMaximize your team’s impact in modern security challenges with a fresh approach that cuts through the noise.


From Classroom to Cybersecurity: Navigatin…
ArticleDiscover Leah White’s transition from teaching to cybersecurity. Delve into the benefits of this career transition and explore how it can lead to growth and fulfillment in both professional realms.




